Industrial giant Honeywell has published its sixth annual report on the threat posed by USB-borne malware to industrial organizations, warning of an increase in sophistication.
The report is based on analysis conducted by the company’s Global Analysis, Research and Defense (GARD) team using data collected by a security product designed to detect and block malware on USB drives used in customers’ industrial environments.
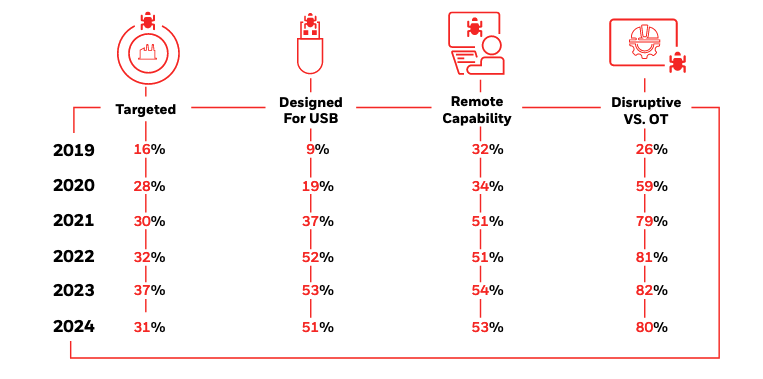
Some data has remained largely unchanged in the past year compared to the two previous years. Of all the malware detected by Honeywell’s product on USB drives, 31% was part of or associated with a campaign known to target industrial systems or companies.
Similar to the past years, more than half of the malware was designed to target or spread via USB drives, which can help the malware cross air gaps. In addition, roughly half of the malware was capable of connecting to a remote C&C server.
Also similar to the past two years, 80% of the detected malware was capable of causing disruption to operational technology (OT) processes, including loss of view, loss of control, or system outages. This includes ransomware, wipers, and malware specifically designed to manipulate or disrupt control, such as Industroyer2 and Black Energy.
“Together, these metrics support the belief that USB-borne malware is intentionally leveraged as part of a coordinated attack campaign against industrial targets, including capabilities that can cause loss of view and/or control,” Honeywell said in its report.
Compared to previous years, Honeywell has started monitoring additional metrics. This revealed a shift towards living-off-the-land (LotL) strategies in an effort to increase attackers’ chances of remaining undetected.
“New evidence indicates that adversaries are pursuing LotL strategies, combining more sophisticated detection avoidance and persistence techniques with execution techniques that leverage the inherent capabilities of the target systems,” Honeywell said.
Roughly 20% of the USB-borne malware was content-based, abusing existing document and scripting functions, rather than exploiting new vulnerabilities.
“Over 13% of all malware blocked specifically leveraged the inherent capabilities of common documents such as Word documents, spreadsheets, scripts, etc. An additional 2% of malware specifically targeted known vulnerabilities in common document formats, and an additional 5% specifically targeted the applications used to modify and create these file types,” Honeywell said.
The company has also seen an increase in malware targeting Linux and other platforms, including ones specifically designed for industrial facilities.
Another concerning trend is related to malware frequency. Honeywell said the amount of malware that was blocked relative to the total number of scanned files has increased by approximately 33% compared to the previous year, which in turn recorded a 700% year-over-year increase.
“For the sixth year in a row, the known threats attempting to enter industrial/OT environments have continued to increase in sophistication, frequency and potential risk to operations,” Honeywell warned. “USB-borne malware is clearly being leveraged as part of larger cyber attack campaigns against industrial targets. This indication is supported by the analysis of ATT&CK techniques, together with the presence of malware associated with major cyber-physical attack campaigns (e.g., Stuxnet, Black Energy, Triton, Industroyer and Industroyer 2).”
The full 2024 Honeywell USB Threat Report is available in PDF format.
Related: ICS Computers in Western Countries See Increasing Attacks: Report
Related: Honeywell Sees Rise in USB-Borne Malware That Can Cause Major ICS Disruption

















